Angry IP scan showed there are 3 active hosts on my network but it didn't identify who or what they are.
Before we go any further its important to document each step of your pentest. You can use any application you like, I chose to use the text editor Kate already installed on Back Track
One of the tools that you will use a lot is Nmap. Nmap is a free security scanner that can do everything from finding live hosts to operating system identification.
Lets run Nmap and see what shows up on my network
Just with a basic scan we can get some idea of whats on the network. Check out the .168 scan results. Notice that nmap showed port 139 netbios is running. This is a pretty clear indication that this target is a windows box.
Notice anything with the .100 target? Check out port 22. SSH, usually this indicates a *nix box
Lets run nmap with a -sS and -sV -O for Syn, Version and OS detection
Woops! That didn't work. I need to be Root to run nmap with those options
Lets try again just at the .100 box since this will be my first target.
This scan shows us some great info. We can see what version of Apache, SSH and other services are running. The scan also identified the target OS as Slax Linux
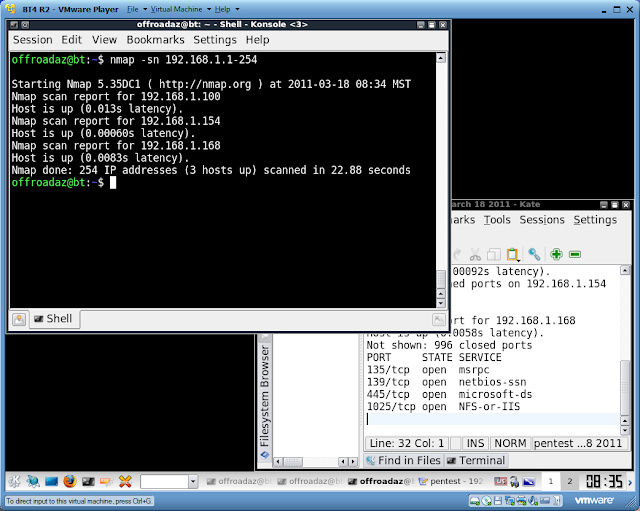
Earlier we used Angry IP Scanner to look for hosts. We can do the same thing using Nmap
Lets run Nmap with the -sn to look for hosts
The results are the same as the Angry IP Scanner. BackTrack has several tools that do basically the same thing. Its really up to you which one you want to learn,




No comments:
Post a Comment